Start Building Your Child’s Credit
The rise of identity theft is among our nation’s most worrisome trends, which doesn’t seem to be dying down. To keep your identity safe, you need to familiarize yourself with the ever-evolving tactics identity criminals use.
This article sheds light on new identity theft types and ways they occur to help you take the necessary precautions. You’ll learn how your private information can be obtained and used for various malicious purposes and what you can do to prevent this.
We’ll also pay special attention to child identity theft as one of the most dangerous forms of this crime. You’ll discover the main reasons children are particularly vulnerable and how to safeguard your young one’s information.
The Many Faces of Identity Theft
Broadly speaking, identity theft is any misuse of someone’s personally identifiable information (PII) for impersonation and personal gain. In 2022, over 40 million American adults were affected by this crime, with an estimated loss of around $43 billion.
Children aren’t safe from this crime either—one in 50 U.S. children falls victim to ID theft annually, which adds another $1 billion to the total losses.
The reason identity fraud is so widespread is the lack of proper PII protection paired with the fact that fraudsters keep finding new ways to steal victims’ information. With this in mind, we can differentiate between seven particularly concerning forms of ID fraud:
- Medical identity theft
- Account takeover
- Social Security number (SSN) identity theft
- Identity cloning
- Synthetic identity theft
- Biometrics hacking
- Child identity theft
Medical Identity Theft

Medical identity theft is an umbrella term encompassing numerous types of fraudulent activity related to someone’s medical information. It can be committed on both ends of the healthcare system:
- Patients/consumers—A fraudster may steal a person’s Medicare number, health insurance account number, or other records to obtain health coverage or illegally purchase prescription drugs. The latter case is common with drug dealers and traffickers who abuse private information to keep stocking up on drugs that can’t be obtained over the counter
- Providers—Healthcare staff might file fake insurance claims to steal reimbursements for medical procedures that never happened. This is either done for personal gain or buffering the costs of providing services to uninsured patients
The best way to avoid the first scenario is to be highly cautious about sharing your medical information. Nobody but you needs access to it, so make sure to keep all relevant documentation safe.
There’s not much you can do to prevent fraud committed by the provider besides trusting they’ll adhere to the regulations imposed by the Health Insurance Portability and Accountability Act of 1996 (HIPAA). The good news is that such theft isn’t particularly common, as most healthcare providers manage patient information responsibly.
Account Takeover
Account Takeover (ATO) has seen an astronomical rise in the past few years. Sift’s Q3 2021 report showed an increase of 307% in ATO cases between 2019 and 2021, while the Q3 2022 report showed a further 131% rise in only the first half of 2022.
Disturbing as these statistics may be, they don’t come as a surprise when you factor in the ever-increasing use of social media and online platforms in general. While ATO can happen in various ways, the general mechanism involves three steps:
- The fraudster steals the target’s login credentials, typically through a cyberattack like phishing or malware
- They change the password and lock the user out of their account
- The scammer impersonates the victim using their accounts, often to obtain money in their name
In most cases, the victim doesn’t realize their account was breached until they try logging into it. The thief may have already abused their account by then, which makes damage control and recovery challenging.
To protect yourself from account takeover, you should follow some simple yet effective cybersecurity practices:
- Use two-factor authentication (2FA) whenever possible—Implementing 2FA gives you another security layer in the form of a one-time passcode sent to a trusted device after you log into your account
- Avoid public WiFi—Public networks are often unsecured, so a hacker can intercept the traffic and steal your credentials
- Log out of accounts on shared devices—If you access your account from a device with multiple users, make sure to log out as soon as you’re done
SSN Identity Theft

SSN theft isn’t new, but it has become harder to resolve over the last decade as a result of the Social Security Administration’s (SSA) decision to start randomizing SSNs in 2011. SSNs of children born after this change no longer have any geographical significance, which makes them more challenging to trace back to the holder.
This is why SSNs—particularly children’s—are highly appealing to fraudsters. A stolen SSN can be used for numerous purposes, including the following:
- Obtaining Social Security benefits in the holder’s name
- Stealing tax refunds
- Creating a new identity (which will be elaborated on later in this article)
SSN theft can have long-lasting consequences because this number is the essence of one’s identity. The best way to recover from it is to change the number, but this is only allowed in a handful of situations. You must prove that you’re suffering ongoing harm and can’t find another way of resolving ID fraud, and the SSA might consider issuing a new number.
To prevent your SSN from being stolen, avoid carrying your Social Security card with you routinely. You should also be careful when filling out forms and leave the SSN out whenever possible.
Identity Cloning
Many ID thefts result in one-off fraud or limited use of the victim’s identity. This isn’t the case with identity cloning, which is far more elaborate and heinous. Instead of stealing specific PII, the perpetrator uncovers as many details about the victim’s life and uses this information to impersonate them.
If successful, identity fraud can make it seem as if two people live identical lives. The fraudster can assume every aspect of the victim’s identity and use it to hide their own.
To prolong the ruse as much as possible, fraudsters sometimes target the identities of children or the deceased. In one of the best-known cases of this crime, a woman spent 28 years living under someone else’s identity.
Signs of identity cloning overlap with those of other theft types because this is a multifaceted crime involving various aspects of your identity. You may notice any of the following:
- Unfamiliar bills in your name
- Changes to your credit score that weren’t caused by your credit activity
- Bounced checks
- Strange correspondence from different authorities or regulatory bodies
If any red flags show up, visit the FTC’s identity theft page to report the fraud and explore your remediation options.
Synthetic Identity Theft
Synthetic identity theft has become especially widespread in recent times, robbing victims and financial institutions of billions of dollars annually. Unlike typical impersonation, it involves the combination of the victim’s real PII and fake information, which creates a new identity that can be exceptionally difficult to track.
This form of fraud is financially motivated in most cases, and it results in fraudulent credit accounts connected to the victim’s identity. The following diagram from the Federal Reserve’s whitepaper on synthetic identity theft detection explains how scammers defraud lenders using synthetic identities:
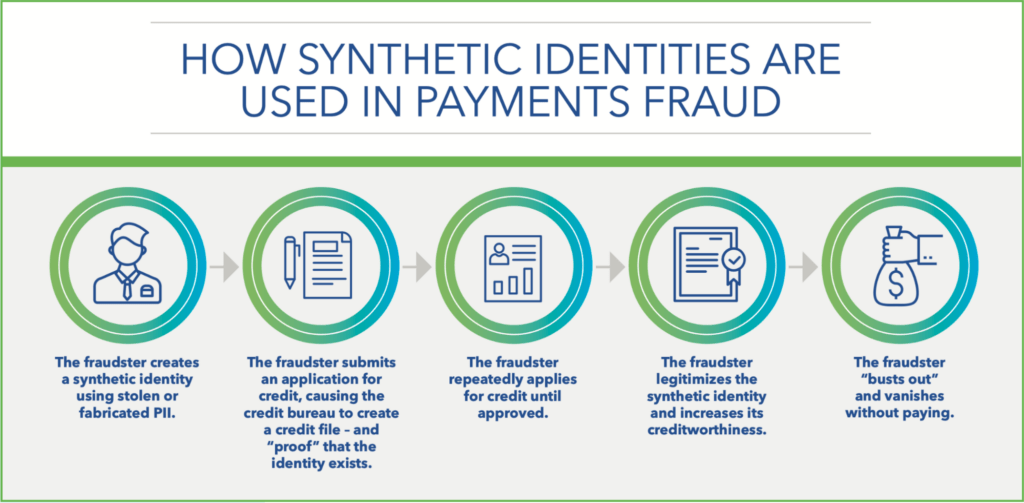
Source: The Federal Reserve: Detecting Synthetic Identities in the U.S. Payment System
Obtaining credit is hard without a credit history, so the scammer creates it by making small purchases and repaying their debt timely. Once they’ve improved their credit profile, the fraudster applies for larger loans and vanishes without paying.
This debt stays connected to the victim’s SSN, so they may be liable for all the charges. While some loans may be discharged under specific circumstances, it’s more common for the victim to end up with excessive debt and a severely damaged credit score.
Proactive and timely credit profile monitoring can be an effective way to minimize the risk of fraudulent accounts. You can do this in two ways:
- Reaching out to the three major consumer credit bureaus (Experian, Equifax, TransUnion) regularly to inquire about your credit
- Signing up for credit and identity monitoring services like FreeKick from Credit Strong
Biometrics Hacking
While biometric authentication is typically considered more secure than traditional credentials, cybercriminals have found several ways to steal biometric data. Facial, fingerprint, and retina scans can be recorded and misused to steal the owner’s identity.
The following table explains some of the most common tactics thieves use to hack biometrics:
| Tactic | How It Works |
| Skimming | A so-called skimmer is placed on a scanner to collect biometric information. This type of theft is commonly used for fingerprints |
| Spoofing | The fraudster replicates someone’s retina or fingerprint so that it looks similar enough to the original |
| Replay attacks | A biometric template is intercepted during authentication and replayed to give the thief access to the account |
Biometrics hacking can be used to steal highly confidential information like bank details and government records. This crime can be difficult to resolve because proving that someone has abused your biometric data is quite challenging.
One of the best ways to protect yourself from hacking is to use multi-factor authentication (MFA). It’s similar to 2FA, except it can involve more than one backup authentication method. The more security layers you have, the harder it is for a hacker to steal your identity, even if they obtain your biometric data.
Child Identity Theft
Children’s identities aren’t subject to comprehensive monitoring and are typically unused. Paired with the aforementioned SSN randomization, this makes them more appealing to criminals than adults’ identities.
A child is unlikely to monitor their credit, so if a fraudster starts a credit profile in their name, they have numerous opportunities to commit fraud before any red flags show up. Parents are often unaware that their children have fallen victim to theft until they’re old enough to start building a credit history and are rejected by lenders.
Other signs of child identity theft include the following:
- Suspicious mail addressing the child (legal notices, bills, pre-approved credit card offers, etc.)
- Notices from the IRS despite the child being claimed as your dependent
- Denial of student aid, government benefits, or Supplemental Security Income (SSI) benefits as a result of someone having obtained them
The most worrisome problem with child identity theft is the lack of proactive security measures. ID fraud is often discovered once the thief has already committed a crime, and there’s not much a parent can do besides staying on the lookout for warning signs.
The best way to avoid subjecting yourself to such constant anxiety is to outsource identity protection. If you need a trusted partner in keeping your child safe from ID theft, FreeKick can help.
Use FreeKick To Safeguard Your Family’s Identities
Identity theft is so widespread that a child’s identity is stolen every 30 seconds, making identity protection services invaluable. That’s where FreeKick by Austin Capital Bank comes in—this two-in-one platform protects your child’s identity and builds credit for them.
How FreeKick’s Protects Your Family’s Identities
FreeKick offers identity protection services for minors, adult children, and parents, making it a comprehensive identity protection package for your whole family. For minors, FreeKick offers the following services:
- Credit profile monitoring
- Social Security number (SSN) monitoring
- Dark web monitoring for children’s personal information
- Up to $1 million identity theft insurance
- Full-service white-glove concierge credit restoration
- Sex offender monitoring—based on sponsor parent’s address
For adult children and parents, FreeKick offers:
- Credit profile monitoring
- SSN monitoring
- Dark web monitoring for personal information
- Up to $1 million identity theft insurance
- Full-service white-glove concierge credit restoration
- Lost wallet protection
- Court records monitoring
- Change of address monitoring
- Non-credit (Payday) loan monitoring
- Free FICO® Score monthly
- FICO® Score factors
- Experian credit report monthly
How FreeKick Builds Credit
FreeKick builds credit for children aged 13 to 25 in three simple steps:
- Create an Account—Sign up on FreeKick.bank and choose a deposit that suits your budget
- Set It and Forget It—FreeKick will start building 12 months’ worth of credit history for your child
- Keep Growing—After 12 months, close the account without any fees (or continue building credit for your child for another year)
These steps give your child the opportunity to have five years’ worth of credit history when they turn 18. This will help them save $200,000 during their lifetimes by giving them access to better loan terms and other financial benefits.
FreeKick Pricing
FreeKick offers two pricing plans:
| FDIC-Insured Deposit | Annual Fee |
| $3,000 | $0 (Free) |
| No deposit | $149 |
Both plans offer:
- Credit building for six children aged 13 to 25
- Identity protection for two parents and six children aged 0 to 25
Secure your family’s identity and financial future—sign up for FreeKick today.
Freekick provides a double dose of financial empowerment and security for your whole family. It helps teens and young adults build strong credit profiles and offers identity motoring for up to two adult parents and six children under 25.





